Talk to Our Technical Experts FREEly — No Pressure, Just Solutions
Get personalized advice tailored to your needs from our trusted experts.
Do You Want a One-Size-Fits-All Solution? Or a Security Strategy Tailored for You?
In today’s fast-changing cybersecurity landscape, generic, prepackaged solutions just don’t cut it. At Zettabrew, we deliver dynamic, policy-driven authorization that adapts to your unique needs.
- Custom-Tailored Security: Flexible and scalable strategies built around your business.
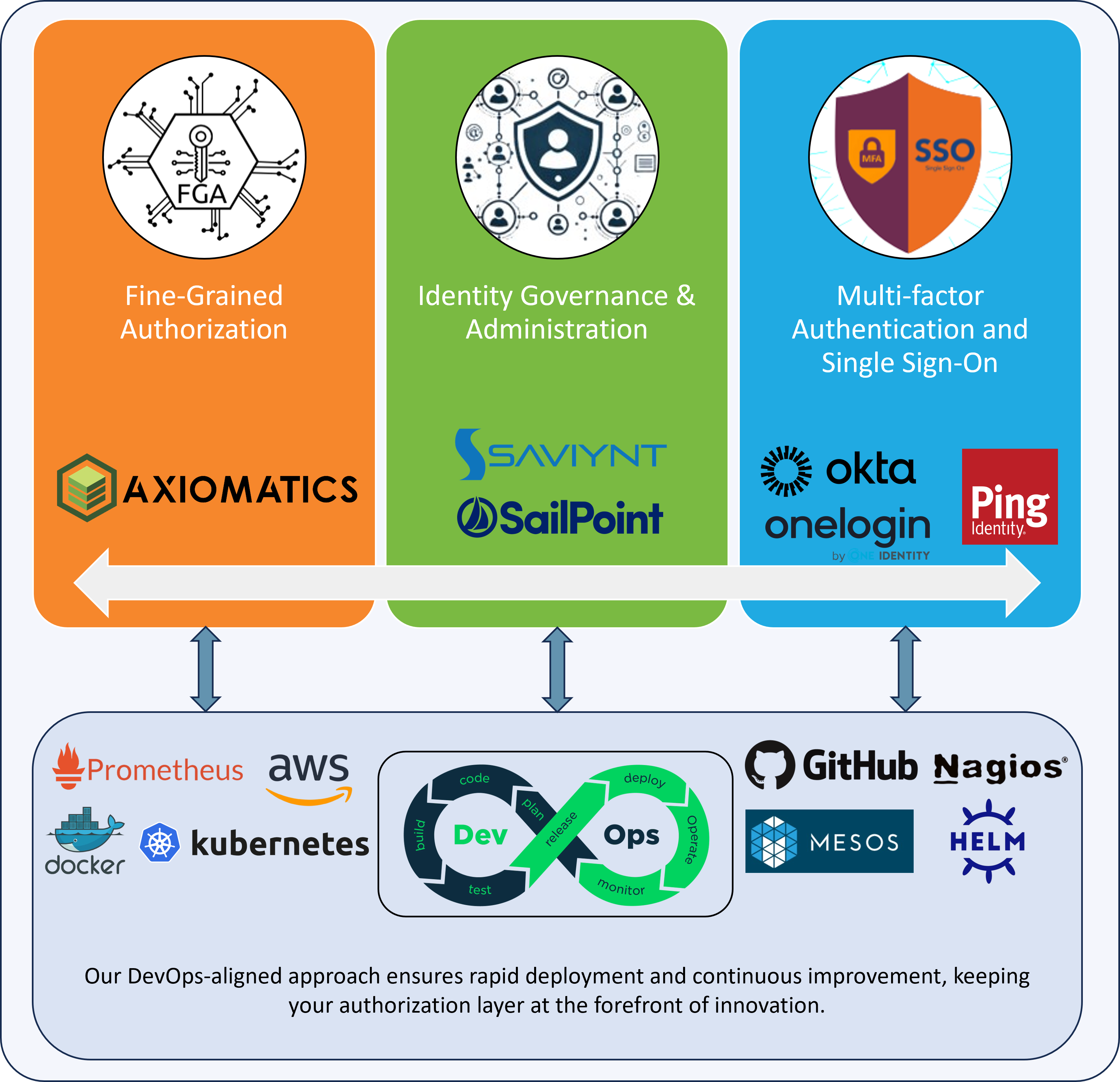
- Fine-Grained Authorization: Seamless integration of Axiomatics into cloud, API, database, and DevOps pipelines.
- Agile Expertise: A lean, specialized team delivering innovative, real-time protection.
Do you want a solution that fits everyone, or one that fits YOU?

Integrate Seamless DevOps Access Control
✔ Policy-Driven Solutions: Embed fine-grained authorization and dynamic access management into your CI/CD pipeline, ensuring regulatory compliance throughout your development lifecycle.
✔ Automated, Scalable Security: Implement Axiomatics-style ABAC and SailPoint identity governance for context-aware, automated access decisions that secure and streamline your DevOps workflows.
✔ Expert DevOps Integration: Leverage our expertise to deploy adaptive access control in hybrid cloud environments, integrating role-based governance and AI-driven identity security to meet zero-trust requirements.
At Zettabrew, we blend deep technical know-how with a consultative approach to deliver tailored solutions that enhance security, boost operational efficiency, and support your business goals. Discover our core service areas:
- Custom-Tailored IAM: Design solutions that ensure only the right people access your critical resources.
- Robust Authentication: Leverage SSO, MFA, and advanced protocols for seamless and secure user experiences.
- Seamless Integration: Enhance security by integrating IAM with existing systems.
- Automated CI/CD Security: Embed policy-driven access control into development pipelines without slowing releases.
- Optimized Workflows: Enhance collaboration and eliminate bottlenecks with streamlined DevOps processes.
- Real-Time Authorization: Deliver dynamic, scalable security tailored for modern development environments.
DevOps Implementation and Optimization Services
Integrating Security into Every Phase
- Automated CI/CD Security: Embed policy-driven access control into development pipelines without slowing releases.
- Optimized Workflows: Enhance collaboration and eliminate bottlenecks with streamlined DevOps processes.
- Real-Time Authorization: Deliver dynamic, scalable security tailored for modern development environments.
- Tailored Cloud Solutions: Design scalable cloud infrastructures that grow with your business needs.
- High Availability: Ensure robust, reliable environments optimized for performance and security.
- Efficient Management: Optimize resource allocation while maintaining stringent security standards.
- Comprehensive Assessments: Identify vulnerabilities and potential risks within your systems.
- Actionable Remediation: Implement clear strategies to enhance your security posture.
- Continuous Monitoring: Maintain compliance and proactively mitigate risks with ongoing oversight.
Security Posture Assessment and Remediation
Proactive Risk Management
- Comprehensive Assessments: Identify vulnerabilities and potential risks within your systems.
- Actionable Remediation: Implement clear strategies to enhance your security posture.
- Continuous Monitoring: Maintain compliance and proactively mitigate risks with ongoing oversight.

Our deep domain knowledge helps reduce your communication overhead by showcasing the areas in which we excel. Discover the industries where our expertise delivers measurable impact and tailored security solutions.
























